- Discoveries Unveiled:
- Between May and September 2023, the ex-Egyptian MP Ahmed Eltantawy encountered an onslaught of Cytrox’s Predator spyware through links transmitted via SMS and WhatsApp, coinciding with his public declaration of intent to run for the presidency in the 2024 Egyptian elections.
- Throughout August and September 2023, Eltantawy’s Vodafone Egypt mobile connection underwent persistent targeting through network injection. Whenever Eltantawy accessed specific non-HTTPS websites, a device positioned at the border of Vodafone Egypt’s network automatically rerouted him to a malevolent website, infecting his phone with Cytrox’s Predator spyware.
- Our investigation, conducted in collaboration with Google’s Threat Analysis Group (TAG), led to the acquisition of an iPhone zero-day exploit chain (CVE-2023-41991, CVE-2023-41992, CVE-2023-41993), tailored to install Predator on iOS versions up to 16.6.1. Additionally, we secured the initial stage of the spyware, which exhibits notable parallels with a Cytrox’s Predator spyware sample obtained in 2021. We attribute the spyware confidently to Cytrox’s Predator with a high degree of certainty.
- Considering Egypt’s established usage of Cytrox’s Predator spyware and the fact that the spyware originated from a device physically situated within Egypt through network injection, we attribute the network injection assault with strong confidence to the Egyptian government.
- Furthermore, Eltantawy’s phone had previously fallen victim to Cytrox’s Predator spyware in September 2023, introduced through a text message featuring a link to a Predator website.
Context:
Ahmed Eltantawy, a former Egyptian Member of Parliament and erstwhile chairman of Egypt’s al-Karama political party, declared his candidacy for the upcoming Egyptian presidential election in March 2023. He articulated his commitment to providing a “democratic” alternative to the incumbent president. Subsequent to this announcement, Eltantawy, along with his family members and supporters, has faced harassment, including the reported arrests of 12 family members.
The current president of Egypt, Abdel Fattah el-Sisi, assumed power in 2014 following a military overthrow of President Mohammed Morsi. El-Sisi has garnered widespread characterization as an autocrat. Human rights organizations such as Amnesty International and Human Rights Watch have extensively documented human rights abuses under el-Sisi’s regime, encompassing repression against civil society groups, activists, and political opposition.
Amid growing concerns about the security of his phone, Eltantawy approached the Citizen Lab for assistance. Conducting a forensic analysis on his device, we identified numerous attempts to target Eltantawy with Cytrox’s Predator spyware.
Notably, the Citizen Lab had previously documented instances of Cytrox Predator infections targeting the devices of two exiled Egyptians: exiled politician Ayman Nour and the host of a prominent news program who opted to remain anonymous.
iOS Zero-Day Exploit Chain Unveiled:
Collaborating closely with Eltantawy, the Citizen Lab and Google’s Threats Analysis Group (TAG) successfully procured an iOS exploit chain designed specifically for his targeted use. Engaging in a responsible disclosure process with Apple, we received the following CVE assignments for vulnerabilities linked to this chain:
CVE-2023-41991 (Security): An illicit app may possess the capability to circumvent signature validation. CVE-2023-41992 (Kernel): A local attacker may potentially escalate their privileges. CVE-2023-41993 (WebKit): The processing of web content might result in arbitrary code execution.
On September 21, 2023, Apple issued updates across various products, effectively patching the vulnerabilities exploited by this chain.
It’s worth noting that zero-day exploit chains targeting mobile devices reportedly command prices in the millions when traded among brokers specializing in these exploits.
Ongoing analysis of this exploit chain is in progress, and a more comprehensive technical report is anticipated for future publication.
Fingerprinting and Probe Activities:
The zero-day chain found its hosting on sec-flare[.]com, concurrently establishing connections with verifyurl[.]me. Employing Internet scanning, we conducted fingerprinting for these two websites, assigning F1 to sec-flare[.]com and F2 to verifyurl[.]me. Through this process, we’ve identified an extensive array of IPs exhibiting matching fingerprints. All IPs, along with domain names retrieved from TLS certificates aligning with our fingerprints, are considered associated with Cytrox’s Predator spyware. While our investigation continues, we are withholding the release of specific domain names or IP addresses at this juncture.
Among the identified domains, some possess names indicative of potential tailoring towards specific countries or regions. These regions include the Arabian Gulf, Southeast Asia, Angola, the Democratic Republic of the Congo, Egypt, Greece, Indonesia, Kazakhstan, Madagascar, Mongolia, the United Arab Emirates, and Sudan – a confirmed Cytrox customer. However, it is imperative to note that we refrain from definitively asserting that all these governments are clients of Cytrox.
Attribution to Predator:
The conclusive component of the iOS exploit chain was an iOS payload. We confidently ascribe this payload to Cytrox’s Predator spyware, drawing on a high level of confidence derived from a comparison with the 2021 sample of Predator that we acquired. A crucial similarity between the two binaries exists, although specific details are redacted to safeguard our ability to monitor future samples.
Furthermore, several of the identified domain names seem tailored to target locations in countries previously recognized as customers of Cytrox Predator, encompassing Egypt, Greece, and Madagascar.
Unraveling the Dynamics of Network Injection
In the months of August and September 2023, as Eltantawy accessed specific non-HTTPS websites through his Vodafone Egypt mobile data connection, a covert redirection occurred, steering him towards a website (c.betly[.]me) via network injection. The domain betly[.]me aligns with our fingerprint F1 associated with Cytrox’s Predator spyware.
The injection was activated based on the specified website in the HTTP Host header, coupled with the value of the User-Agent header.
The destination website’s content comprised two iframes. The first, with ID “if1,” displayed seemingly harmless content as bait (in this instance, a link to an APK file devoid of spyware). The second, with ID “if2,” constituted an invisible iframe containing a Predator infection link hosted on sec-flare[.]com.
Focused Spyware Injection Within Egypt
In our testing, we sought to identify the specific network location of the injection. Ultimately, our efforts led to pinpointing the injection to a connection between Telecom Egypt and Vodafone Egypt. The technical data alone does not definitively indicate whether the middlebox is situated on the Telecom Egypt side or the Vodafone Egypt side of the link. However, we lean towards the suspicion that it resides within Vodafone Egypt’s network. This suspicion arises from the precise targeting required for injecting content at an individual Vodafone subscriber, suggesting potential integration with Vodafone’s subscriber database.
Considering the injection’s operation within Egypt, the spyware’s sale to government agencies, and Egypt’s established history as a Predator customer, it becomes highly improbable that this targeting and setup unfolded beyond the scrutiny of Egyptian authorities.
Procedure for Pinpointing the Source of Spyware Injection
Typically, the localization of an injection involves sending packets from the targeted device (the “client”) with increasing IP “Time To Live” (TTL) values. As routers subtract one from the TTL for each handled packet and usually identify their IP addresses to the sender when handling an expired packet, this method allows the identification of routers on either side of the injector. These routers include the one reporting an expired packet with the highest TTL for which the injector does not respond and the one reporting an expired packet with the lowest TTL for which the injector does respond. The network to which the IP addresses belong can then be identified through an IP WHOIS database lookup.
Inapplicability of Traditional Technique: However, in Eltantawy’s case, this technique was not applicable due to the presence of a separate middlebox in Vodafone Egypt’s network, located close to subscribers, managing all TCP connections. This middlebox, suspected for benign traffic management, is situated at approximately IP TTL = 4 from Eltantawy. As the middlebox rewrites packets with fixed TTL values, control over the TTL value beyond the traffic management middlebox is lost. Nevertheless, it was determined that the spyware injection was not located up to TTL = 4 from Eltantawy.
Alternate Localization Technique Enabled by Injector Design Choices: Two design choices in the injector facilitated a reverse localization process from a controlled measurement server. Firstly, the injector attempts to conceal its presence by copying received IP TTL values into injected packets. Secondly, when injecting a response “from” a server to a client, the injector uses the server’s TTL from the first SYN/ACK for a TCP connection, disregarding TTL values in subsequent SYN/ACKs.
Combined, these design choices enable the use of the measurement server to “prime” the injector for injecting a TTL = 1 packet to the client. This involves responding to a SYN with a SYN/ACK reaching the injector with TTL = 1 and sending a follow-up SYN/ACK with a somewhat higher TTL to reach the traffic management middlebox, complete the connection, and prompt the middlebox to send the HTTP GET request triggering the injection.
Upon the HTTP GET request reaching the injector, a packet with TTL = 1 is sent back to the client. As the injector is not directly adjacent to the client, the downstream router immediately identifies the packet as expired and notifies the sender of the injected packet. Since the injector spoofs the packet to come from the measurement server, the router identifies itself to us, informing our measurement server of the packet’s expiry.
Assigning Attribution to the Injector
Our confidence in attributing the spyware injection in Egypt to Sandvine’s PacketLogic product is supported by a three-part analysis.
Part One: Characterization of Spyware Injection in Egypt Describing the spyware injection in Egypt posed challenges due to the presence of the Traffic Management Middlebox on Vodafone Egypt’s network, hindering direct observation of raw packets sent to Eltantawy’s device. Nevertheless, we identified the spyware injection’s characteristics:
- The injected HTTP response to the client is a “307 Temporary Redirect” with the “Via: 1.0 middlebox” header set, accompanied by a single TCP RST packet to the server.
- The injector re-sends an identical packet up to four times if unacknowledged, followed by a final terminating packet if the packet remains unacknowledged after five sends.
- The injector sets TCP window size to 32120 in injected packets.
Part Two: Egypt Spyware Injection Behavior Matches New Behavior from Devices in Turkey Previously Attributed to Sandvine Observing that the behavior aligns entirely with Turk Telekom’s network injection capability, previously attributed to Sandvine’s PacketLogic devices, reinforced our attribution. Although the injection no longer precisely matched our 2018 Sandvine PacketLogic fingerprint, it consistently mirrored the Egypt malware injection:
- The injected HTTP response to the client is a “307 Temporary Redirect” with the “Via: 1.0 middlebox” header set, alongside a single TCP RST packet to the server.
- The injector re-sends an identical redirect packet up to four times, with a one-second delay in between sends, and sends a final terminating packet if unacknowledged after five sends.
- All injected packets maintain a TCP window size of 32120.
Part Three: Devices in Turkey Previously Attributed to Sandvine Have Old Bug and Quirks Despite New Behavior As of September 2023, the Turk Telekom injector retains an odd bug observed in their Sandvine PacketLogic deployment in December 2020. This consistent behavior, including injecting HTTP 307 Temporary Redirect messages in response to a TLS Client Hello, aligns with characteristics of our 2018 Sandvine PacketLogic fingerprint. Additionally, the injector exhibits traits such as injecting HTTP 307 Temporary Redirect messages in FIN/ACK packets, setting TCP window size to 32120, and injecting a single TCP RST packet to the server concurrently with the redirect to the client—all in line with our 2018 Sandvine PacketLogic fingerprint.
Conclusion: Egypt Spyware Injector is a Sandvine PacketLogic Product The compelling similarities between the Turk Telecom injector’s past behavior, previously attributed to Sandvine PacketLogic, and its current behavior consistent with the Egypt spyware injector lead us to confidently attribute the Egypt spyware injector to Sandvine PacketLogic.
Engaging in SMS-based Targeting
Furthermore, Eltantawy received various SMS notifications in September 2021, May 2023, and September 2023, disguising themselves as messages originating from WhatsApp.
These deceptive messages urged Eltantawy to click on an enclosed link to “terminate” what the messages claimed was a new login to his WhatsApp account. In actuality, clicking on these links would probably have resulted in Eltantawy’s phone being infected with Cytrox’s Predator spyware.
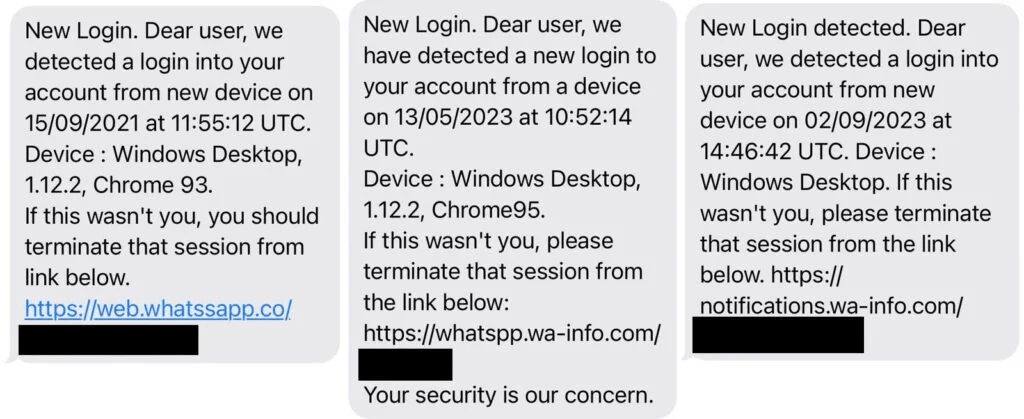
Curiously, the domain names embedded in the links do not align with our F1 or F2 Predator fingerprint. Nevertheless, approximately 2 minutes and 30 seconds after Eltantawy accessed the message on September 15, 2021, the Predator spyware became active on his phone. Our suspicion is that he clicked the link in the message, triggering the installation. Given the similarity in bait content present in the 2023 messages, we infer that these messages were also endeavors to install the Predator spyware on his phone.
We posit that these websites are bespoke, potentially registered by a specific Predator customer. The following domain names are presumed to be interconnected:
- almal-news[.]com
- chat-support[.]support
- cibeg[.]online
- notifications-sec[.]com
- wa-info[.]com
- whatssapp[.]co
- wts-app[.]info
Conclusion
The deployment of mercenary spyware to target a prominent member of a democratic opposition, especially after declaring their candidacy for the presidency, constitutes a clear interference with free and fair elections and a violation of fundamental rights such as freedom of expression, assembly, and privacy. This action directly contradicts the public justifications often presented by mercenary spyware firms.
President el-Sisi has faced widespread condemnation for his autocratic rule, and Egypt’s well-documented human rights abuses underscore the need for vigilance by any responsible company whose technology could be exploited. However, our report indicates that insufficient due diligence was conducted to prevent such abuses by Cytrox and other identified firms whose technology was utilized to target and compromise Eltantawy’s device.
This latest incident adds to the troubling history of abuses associated with Cytrox and its Predator spyware. In addition to the hacking of the devices of other Egyptians using Predator spyware, our documentation includes instances such as the hacking of Greek journalist Thanasis Koukasis and former Meta employee Artemis Seaford, a dual Greek-American citizen. Further investigations revealed the use of Predator spyware in hacking the devices of sitting European Parliament member Nikos Androulakis and its sale to human rights violators, including the genocidal militia in Sudan. Consequently, in July 2023, the US Commerce Department placed Cytrox on the list of mercenary spyware firms in its designated entity list.
Our report also sheds light on potential vulnerabilities throughout the telecommunications ecosystem, particularly at the network layer, which can be exploited to inject malware into unsuspecting users’ devices. The internet’s routing through various networks and middleboxes, especially those lacking cryptographic protection for network requests, poses security risks. Despite recent progress in encrypting web communications, occasional visits to non-HTTPS websites can still result in spyware infections. This report underscores the critical need for achieving a 100% adoption rate of HTTPS.
With high confidence, our report concludes that a Sandvine PacketLogic device played a role in injecting a redirect to malicious code in response to an internet request made by Eltantawy. This redirect subsequently delivered zero-day exploits in an attempt to infect his device with Cytrox’s Predator spyware. This marks a recurrence of the abuse of Sandvine’s products, as previously documented in 2018 when malicious redirects were injected into victims’ web traffic in Turkey. Despite prior public awareness and communication with Sandvine regarding the identified abuses, it appears that Sandvine’s product is still being misused in Egypt. We have notified Sandvine of our findings and committed to publishing any response received; as of the publication date, no reply has been received.
This case prompts inquiries into the inadequacy of controls surrounding the export of technologies with potential human rights violations. Instances of technology companies headquartered in Canada being implicated in the export of technologies violating international human rights law have raised concerns. While Canada has pledged to uphold controls on commercial spyware technology through a recent Statement of Principles, tangible actions and regulations addressing human rights and export controls for dual-use technology are yet to be implemented.
Specifically, our recommendations include urging the Canadian government to establish laws and effective sanctions preventing the export of technologies to jurisdictions with a likelihood of human rights abuses. Additionally, transparent reporting on Canadian dual-use exports, including detailed information on the exported items, exporting companies, and end-users, is essential for public accountability. Canadian companies should also be subject to human rights due diligence obligations enforced by law, accompanied by appropriate penalties.
Ensure Immediate Updates for Apple Devices and Activate Lockdown Mode
We strongly recommend that individuals promptly update their devices.
The updated versions include: macOS Ventura 13.6, macOS Monterey 12.7, watchOS 9.6.3, watchOS 10.0.1, iOS 16.7 and iPadOS 16.7, iOS 17.0.1 and iPadOS 17.0.1.
Similar to the recently disclosed BLASTPASS zero-click exploit, we are of the belief, and Apple’s Security Engineering and Architecture team has confirmed to us, that activating Lockdown Mode effectively thwarts this specific attack.
These recent instances underscore the significant protective value offered by this security mode.
Therefore, we advise all Mac, iPhone, and iPad users, particularly those facing heightened risks due to their identity or activities, to enable Lockdown Mode.

